Engage cybersecurity leadership to keep your business projects on track while improving your cybersecurity program. Your internal stakeholders can collaborate with your vCISO, taking advantage of proven experience to create a cybersecurity strategy and roadmap for improving your organization’s cyber risk posture and upgrading your defenses.
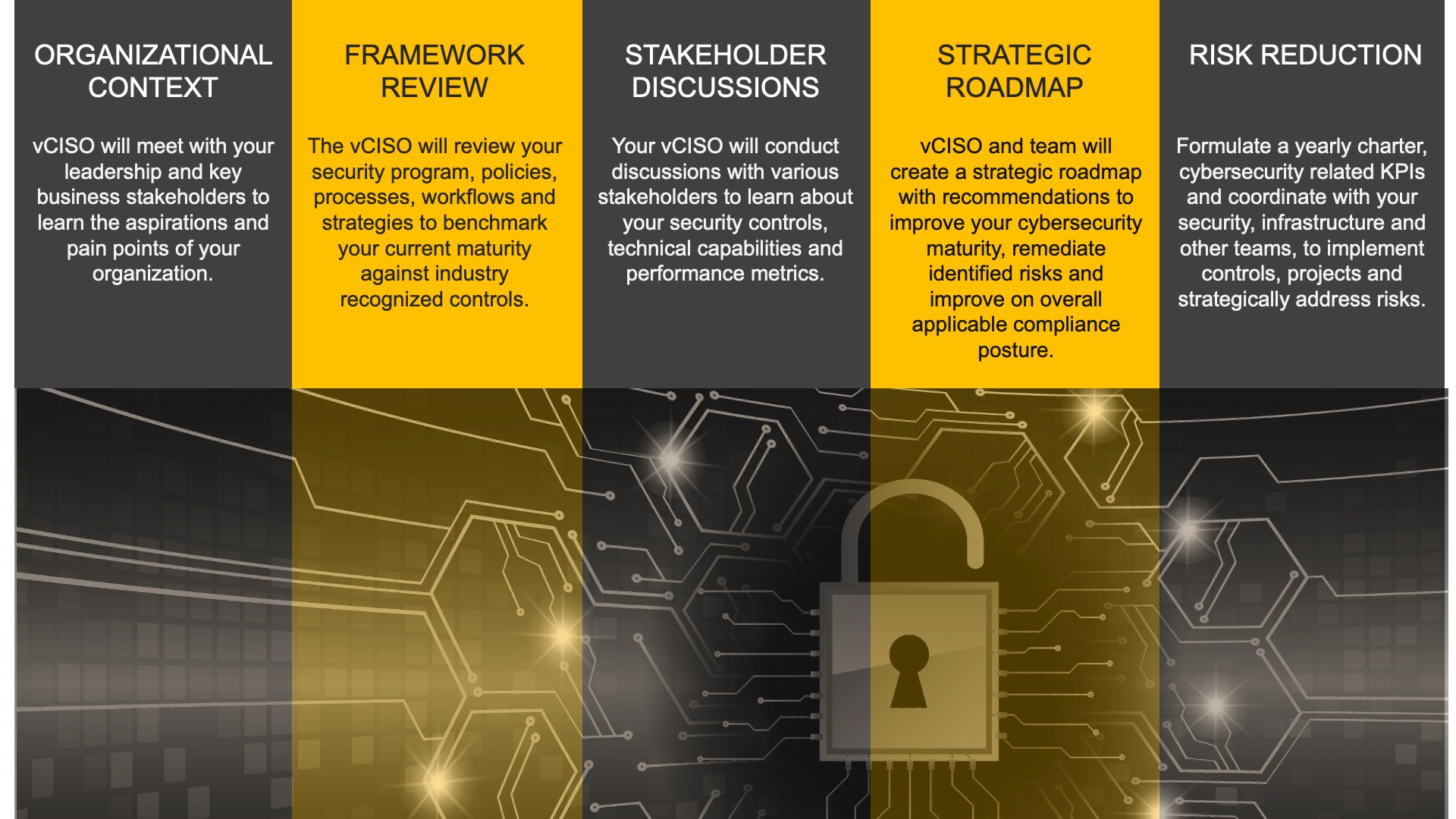
RETAIN A CYBER RISK EXPERT
Establish clear data protection policies and procedures. This includes:
- Defining roles and responsibilities for data oversight.
- Integrating privacy practices into human resources, operations, and IT policies.
- Regularly reviewing internal practices through audits and assessments.
CONFIDENTLY MANAGE BOARD DISCUSSIONS
Integrate privacy considerations into the design and development of all systems and services:
- Minimize the collection and retention of personal data.
- Limit access to only what is necessary for specific tasks.
- Build privacy features into systems from the ground up.
FOCUS ON YOUR BUSINESS GROWTH
Organizations must ensure clarity and accountability in how personal data is used. Our approach supports:
- Clear communication with individuals about how their data is processed.
- Tools and processes that allow users to access, correct, or monitor the use of their information.
IMPROVED CONFIDENCE WITH LOWER COST
Carry our detailed risk assessments for systems or processes that involve significant data processing:
- Identify potential impacts on data privacy and security.
- Recommend mitigation strategies before deployment or major changes.