Data Protection Considerations
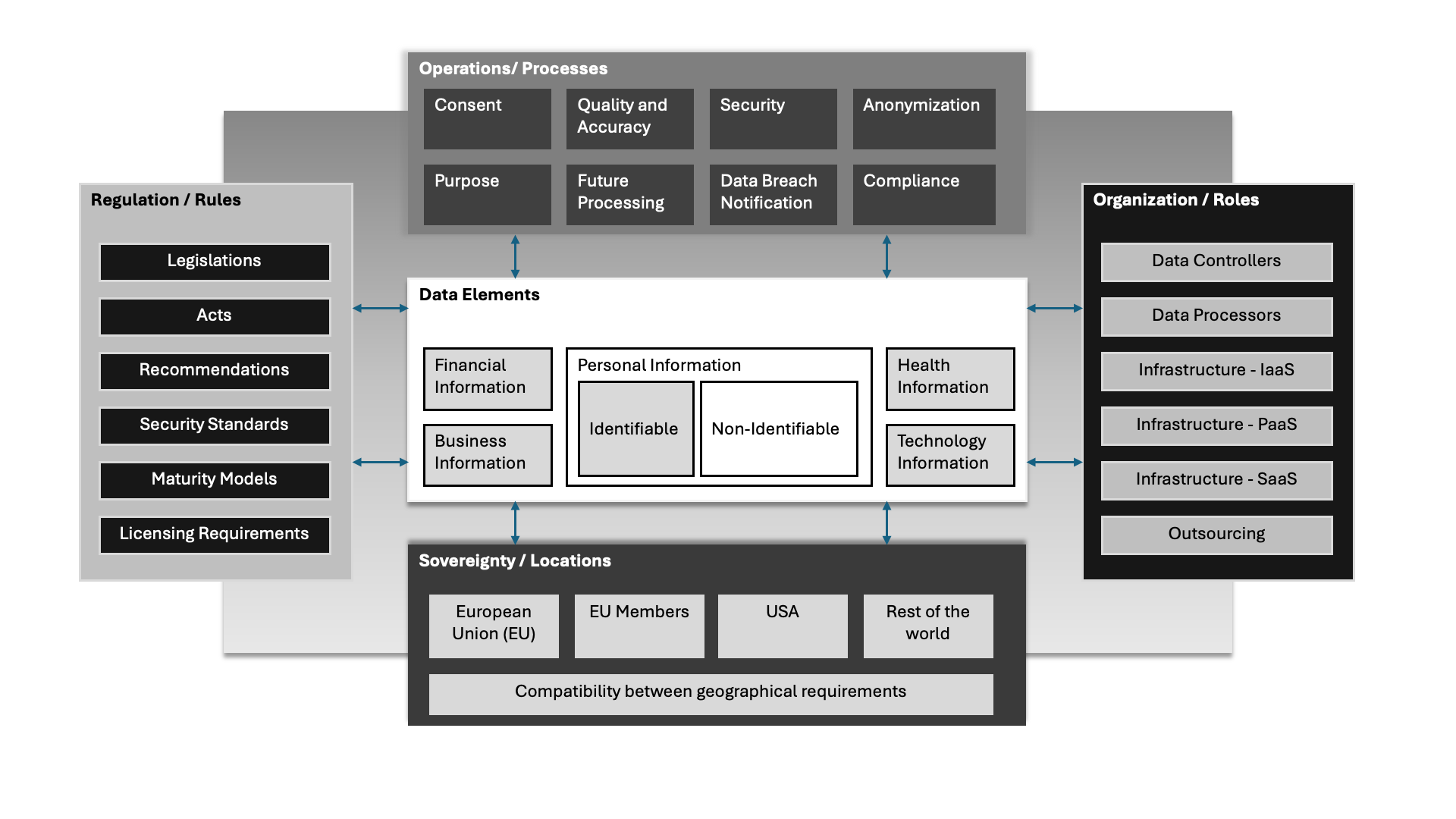
With the increasing data elements stored, processed and/or transferred in a structured and un-structured manner, it is becoming more complex for adhering to various regulations, security standards, guidelines, etc. Our data protection considerations provide a glimpse of what organizations must do to protect data, their reputation as a brand, and possible financial and non-financial impact it can cause.
We suggest a six (6) stage approach to address the foundational issues related to data protection.
Strong Governance and Internal Controls
Establish clear data protection policies and procedures. This includes:
- Defining roles and responsibilities for data oversight.
- Integrating privacy practices into human resources, operations, and IT policies.
- Regularly reviewing internal practices through audits and assessments.
Privacy by Design and Default
Integrate privacy considerations into the design and development of all systems and services:
- Minimize the collection and retention of personal data.
- Limit access to only what is necessary for specific tasks.
- Build privacy features into systems from the ground up.
Transparency and User Empowerment
Organizations must ensure clarity and accountability in how personal data is used. Our approach supports:
- Clear communication with individuals about how their data is processed.
- Tools and processes that allow users to access, correct, or monitor the use of their information.
Risk Based Assessments
Carry our detailed risk assessments for systems or processes that involve significant data processing:
- Identify potential impacts on data privacy and security.
- Recommend mitigation strategies before deployment or major changes.
Continuous Security Enhancement
Security is not a one-time activity. Organizations should continue the implementation of:
- Evolving technical safeguards tailored to modern threats.
- Ongoing evaluation and updates to infrastructure and procedures.
- Secure-by-default configurations that adapt to changes in technology and business needs.
Culture of Data Protection
Organizations should embed a data protection mindset across all levels:
- Conduct training and awareness initiatives.
- Encourage a culture of accountability and continuous improvement.
- Implement mechnisms to recognize and reward individuals for demonstration of data protection centric behaviors